Cloud security software assesses your company’s security risks online and protects your business’s networks, information, and systems against malicious attacks.
This article discusses the 18 best cloud security software you can use today to monitor and automate security checks across apps, users, devices, and networks.
Let’s dive in.
18 Best Cloud Security Software
1. Netskope Cloud Security Platform
Netspoke is a leader in the field of cloud, data, and network security services. They simplify your operations by enabling hybrid work, redefining data protection, and helping you realize the full potential of your cloud applications.
They provide real-time security without compromising performance.
Their solutions include, among others:
- Ultra-fast security cloud platform
- Security Service Edge (SSE)
- Next-Gen Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- Cloud Exchange
- Public Cloud Security
- Advanced Analytics
- Cloud Firewall
- Data Loss Prevention (DLP)
- Digital Experience Management
- Remote Browser Isolation
- SaaS Security Posture Management
- IoT Security
2. Broadcom CloudSOC CASB

According to Broadcom, CloudSOC CASB is a comprehensive cloud security software.
It works with Symantec Data Loss Prevention (DLP), Symantec DLP Cloud Detection Service (CDS), and DLP Cloud Service for Email.
The software can track and govern user activity in different apps, including Google G Suite and Office365.
It can also implement controls over data stored in the following:
- Servers
- Endpoints
- File shares
- Databases
- SharePoint
You can also use it to respond to security incidents, maintain regulatory compliance, and safeguard your data on the web.
3. Trend Micro Cloud App Security
Trend Micro Cloud App Security is software that detects ransomware, business email security compromise, and online attacks.
Integrating it into your system is easy, and it can detect both incoming and internal phishing attacks.
In 2021, the software detected as many as 25.7 million email threats that escaped the security barrier provided by Microsoft Office 365 and Google Workspace.
During the same year, it blocked over 94 billion threats.
It is easy to say they know what they are doing.
4. StackHawk Security Testing Software
API and Application Security Automation software StackHawk believes software testing is a part of security testing.
StackHawk Security Testing Software detects your API security risks and helps you mitigate any bugs in your APIs before shipping them out.
The testing is automated and configured through code. It can be custom-built to suit your needs.
The automated system enables your engineering team to review the vulnerability details immediately and fix any flaws in the system.
StackHawk is easy to set up. As a cloud security software, it is a relatively cheap solution.
5. Nevatech Sentinet
Nevatech’s Sentinet software combines API Governance design-time and API Management run-time capabilities.
It supports all standard communication systems on-premises or in the cloud. Other main features include the following:
- It makes API Management simple
- You can integrate your APIs and services with those of your partners
- It offers a fully customizable developer portal
- You can manage your content management system through it.
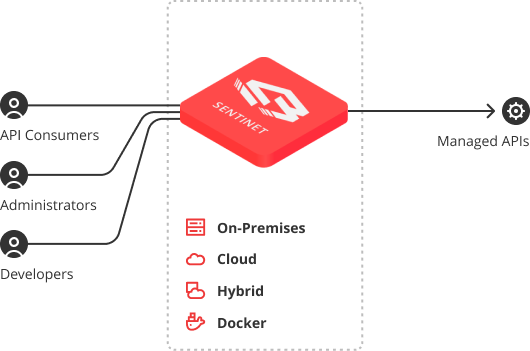
6. Reblaze
Cloud security firm Reblaze offers security technologies in a single platform. It runs in a dedicated VPC (Virtual Private Cloud) and provides services in the following 7 key cybersecurity areas:
- Global CDN (Content Delivery Network) Integration
- DDoS (Distributed Denial-of-Service) Protection
- Bot Management
- Web application firewall
- Real-time traffic control
- API security
- ATO (Account Takeover) prevention
Using Reblaze as your security software has the following benefits:
- Your content delivery system is really fast
- Your website performs better
- CDN can serve your site even if your server is temporarily down
- You can build the most robust site possible
7. Cato SASE Cloud with SSE 360
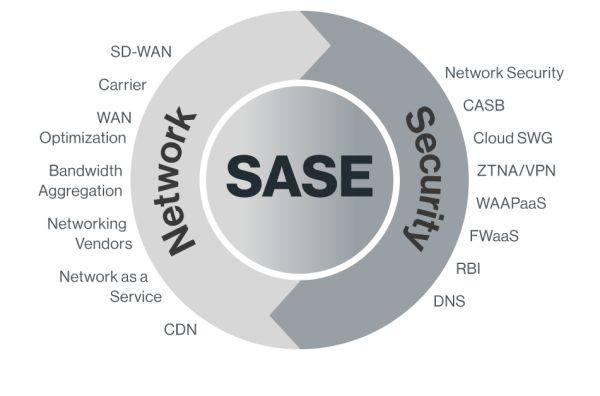
Cato’s security stack, SSE 360, is built upon its single-pass security engine architecture. It features the following:
- Secure Web Gateway (SWG)
- Cloud Access Security Broker (CASB)
- Data Loss Prevention (DLP)
- Zero Trust Network Access (ZTNA/SDP)
- Firewall as a Service (FWaaS)
- Advanced Threat Prevention
It can detect security compromises through its MDR or Managed Threat Detection and Response service. MDR uses machine learning algorithms to detect security compromises.
8. Beagle Security
You can identify your website’s vulnerabilities and security weaknesses through Beagle Security‘s platform and fix them immediately.
It allows you to evaluate your website from a hacker’s perspective to understand its security flaws. Before suggesting security correction, it provides you a score of the flaws based on their severity so that you know what is at stake.
The software works with all types of websites and frameworks. It is developer-friendly (integrate it into the DevOps pipelines) and can automate workflows by scheduling tests for you.
If you own a WordPress website, you can secure it with Beagle security. Beagle software can test your website’s codes to prevent data thefts and cyberattacks.
Signing up for Beagle is free. Besides, you can choose from four awesome paid plans starting at $40.84/month.
9. API Security and Legal Risk Management Software
Created by security researchers from USA and Canada, TeejLab’s API Security and Legal Risk Management software applies data science and machine learning to cloud security.
The company claims to have built the world’s first software composition analysis system. That means they can discover any shadow/hidden and public/private APIs to understand the threat your online assets are facing.
The software works through sis ‘managers.’ They are:
- API Discovery Manager
- API Security Manager
- API Consumer Manager
- API Producer Manager
- API Lifecycle Manager
- API Community Manager
10. Wallarm End-to-End API Security Platform
Wallarm’s End-to-End API Security solution protects your API and online applications in the cloud environment.
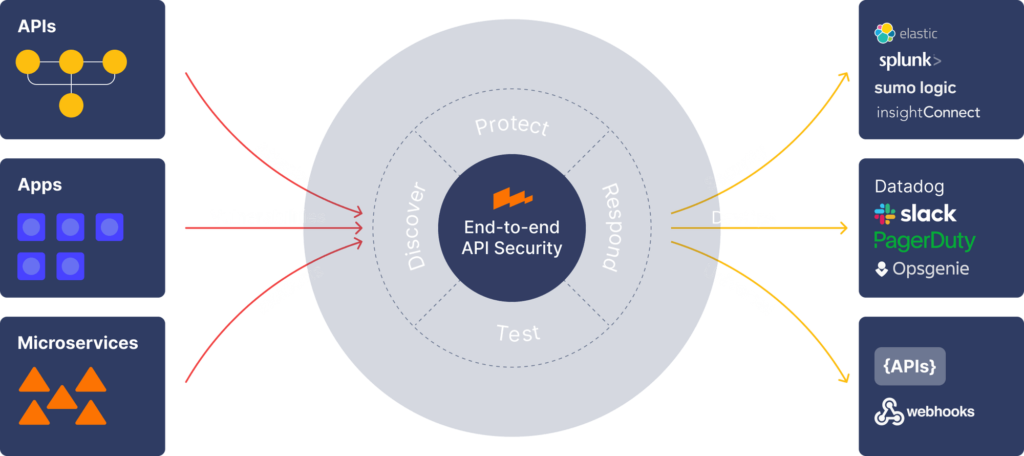
Wallarm offers the following four distinct security products to choose from:
- End-to-end API Security
- API Security Platform
- Advanced API Security
- Cloud-Native WAAP (web application and API protection)
This software protects any API, including REST, SOAP, graphQL, gRPC, microservices, and web applications.
And you can do that in any cloud environment, including the following:
- AWS
- GCP
- Azure
- IBM Cloud
- Private cloud
- Hybrid cloud
- Multi-cloud
- Service Mesh
- Inline
The security threats Wallarm can protect you from include:
- API-specific threat
- DDoS
- Bots
- Software and data integrity failures
- Insecure design
- Server-side request forgery
- Insufficient logging and monitoring
- Broken access control
- Security misconfiguration
- Cross-site scripting
- Sensitive data exposure
They are already serving e-commerce, health, fintech, and technology companies. They can be your choice if you want to keep your cloud presence safe.
11. Drata Platform
Drata is your go-to security and compliance automation platform for continuously monitoring your company’s security controls. It makes your cloud entities ready for audit.
The compliance frameworks Drata works with:
- SOC 2
- GDPR
- ISO 27001
- HIPPA
- PCI DSS
- NIST CSF
- NIST SP 800-53
- Microsoft SSPA
- NIST SP 800-171
- FEIEC
- CMMC
You can build your personal security and standard framework with Drata to suit your business goal.
As your business grows, so does the need for setting a standard so that you can serve your customers better.
Besides, when a compliance framework changes, you need to change your compliance program too. You can easily do that by subscribing to Drata.
20 prominent companies or platforms you can connect to Drata:
- Cloudflare
- Azure DevOps
- ADP OIDC
- Amazon Web Services (AWS)
- Asana
- Checkr
- Datadog
- DigitalOcean
- DocuSign
- Okta
- GitHub
- Office365
- Google Cloud Identity
- Google Cloud Platform
- Google SAML
- Google Workspace
- JumpCloud
- Microsoft AD FS
- Microsoft Azure
- Microsoft Teams
12. Vanta Security Platform

Vanta is another compliance software you can use to prepare your business for compliance audits.
It works with security and privacy frameworks such as SOC 2, CCPA, ISO 27001, OFDSS, FedRAMP, PCI DSS, HIPAA, US Data Privacy, and GDPR.
You can also implement a custom and in-demand security framework for your business through it.
Using this software, you can continuously monitor your cloud systems, security measures, tools, and people to ensure that you remain compliant.
The software will tell you how many issues need your attention and whether they are related to your people, engineering steps, policy, or risks.
Vanta platform does the following for you:
- It continuously monitors your tools and services to ensure you remain compliant with the standard
- It alerts you in real-time so you can fix the issue
- Keeping customer data secure is a must for any business. Vanta helps you accomplish that
- You can create your custom framework of standards to keep your business ahead of the game
You can integrate the Vanta platform with about a hundred platforms or tools, including the following:
- Azure
- Crowdstrike
- Asana
- AWS
- Workday
- Trello
- Slack
- Snowflake
- Square
- Office365
- Monday
- Google Cloud
- GitHub
- Datadog
- Confluence
- DigitalOcean
13. Wiz Cloud Security Posture Management
Cloud security posture management platform Wiz automatically evaluates over 1,400 configuration rules to identify a cloud entity’s vulnerabilities and suggest real-time remedies.
Some of the smart companies that are already using Wiz to secure their presence on the cloud include:
- Salesforce
- Priceline
- Fox
- Morgan Stanely
- Snowflake
- BMW
- Slack
You can connect your operating systems and applications with Wiz in minutes and start monitoring them for vulnerabilities.
Using the Threat Center, you can identify any emerging threats to keep your applications and products safe.
Then, with a click, you can apply the remediation action to neutralize those threats with little help from the automation setup.
Read how Priceline contextualized the compliance of its internet cloud infrastructure with Wiz.
14. Sprinto Security Compliance Solution
Sprinto is a security compliance solution for cloud companies. It is an integration-first, automation-enabled, and audit-aligned platform.
Primarily, Sprinto works with two standards frameworks:
- SOC 2
- ISO 27001
But it also supports other compliance frameworks such as:
- GDPR
- CIS
- FCRA
- PCI-DSS
- HIPPA
- NIST
- CSA Star
- ISO 27017
- OFDSS
- CCPA
Major features of Sprinto cloud security software include the following:
- It has an integrated audit process portal where you can audit your apps, products, and systems quickly.
- You can share your security posture with your stakeholders safely from the portal.
- You can monitor the security controls in place continuously to know you are compliant.
- Incident management is easier with Sprinto as it is designed to suggest prompt action.
- Sprinto offers role-based access to the security system. Employees may be given access to the platform as full-time workers, contract workers, and freelancers.
- The platform assigns tasks based on their priorities. Critical tasks must be completed before attending the due and failing categories.
15. Check Point Cloud Email & Collaboration Suite Security
Check Point’s Harmony Email & Collaboration Security offers Office365 and Google Workspace cloud security.
It stops malware and ransomware from reaching your inbox, prevents sensitive data from leaving your system, and secures accounts from being maliciously taken over.
It also offers file-sharing security against malware, ransomware, and east-west attacks. With this security in place, you can use Dropbox, Sharefile, Google Drive, and SharePoint, knowing your communications are safe.
In addition, Harmony Security also adds a layer of security to third-party collaboration applications like Slack and Microsoft Teams.
The software uses 300+ indicators to detect phishing and can reduce phishing reaching your inbox by 99.2%.
16. Laika
Compliance automation software Laika supports SOC 2, ISO 27001, PCI DSS, GDPR, HIPAA, and HITRUST.
Automating compliance saves you valuable time and money. It can monitor your vendor activities, communications, and security controls to ensure you stay compliant.
Laika can also help you to build a scalable compliance program for your organization. A custom program is required as you grow as a company and business relations and transactions become more complex.
On its way to ensuring compliance for your organization, Laika takes four well-defined steps. They are:
- Onboarding. Connect your apps and cloud systems to Laika in minutes.
- Implementation. Supported by integrated workflows, masterfully implement the compliance steps, including penetration testing.
- Audit. Evidence-gathering required for the audit is automated, which makes the audit process fast and effective.
- Staying Compliant. Now that you are compliant, continue the process to stay alert and compliant.
17. Symantec Cloud Secure Web Gateway
Broadcom’s Symantec Cloud Secure Web Gateway, formerly Web Security Service (WSS), is a cloud-delivered web security for all Symantec-protected customers.
Since more and more apps and businesses are moving to the cloud, it has become important to develop security programs to protect data on the cloud.
To that end, Symantec Cloud Secure Web Gateway offers several market-leading capabilities, including the following seven:
- Data loss prevention
- Email security
- Web isolation
- Sandboxing
- Anti-virus scanning
- Software-defined perimeter
- Cloud-hosted proxy
Read here how the Tolly Group validated Symantec SASE performance.
The Cloud Secure Web Gateway is an all-in-one platform providing you with the protection you need by preventing emerging threats before they reach your systems and helping you stay compliant.
The software maker believes in simplifying the security process.
You start by enhancing your arsenal with anti-phishing and anti-malware capabilities.
You scan your system with your capabilities.
Then it is time to make sure no sensitive or proprietary data leaves your organization.
Can malware remain hidden in the encrypted traffic? You need a strong SSL inspection to find that out.
Once the system is secure, enforce security and Governance policies to stay secure and compliant.
These all can be done from the same Cloud Secure Web Gateway.
18. Acronis Cyber Protect Cloud
Acronis Cyber Protect Cloud, or all-in-one cyber protection, is for cloud security service providers. The platform offers several tools to ensure a business’s presence on the cloud is safe.
It uses AI-based anti-malware and end-point protection management in one platform to simplify the cloud security system, thus helping businesses give more time to productivity.
Acronis’s Advanced Cyber Protect Packs include the following services:
- Advanced security
- Advanced backup
- Advanced disaster recovery
- Advanced email security
- Advanced data loss prevention
- Advanced file sync and share
- Advanced management
Cloud Security: 5 Books
AWS Security, by Dylan Shields.
Cloud Security Career Handbook: A beginner’s guide to starting and succeeding in Cloud Security, by Timothy Isle.
CCSP (ISC)2 Certified Cloud Security Professional Official Study Guide & Practice Tests Bundle, by Ben Malisow.
Cloud Security Handbook: Find out how to effectively secure cloud environments using AWS, Azure, and GCP, by Eyal Estrin.
AWS Certified Security – Specialty Exam Guide: Build your cloud security knowledge and expertise as an AWS Certified Security Specialist (SCS-C01), by Stuart Scott.